AWS VPC vs Azure VNet: A Complete Multi-Cloud Networking Guide
AWS VPC vs Azure VNet: As cloud adoption continues to grow, multi-cloud architectures using both AWS and Azure are becoming increasingly common. Companies choose a multi-cloud strategy for cost advantages, resilience, compliance, and flexibility. But the foundation of any multi-cloud approach is networking, and that is where understanding AWS VPC and Azure VNet becomes essential.
This blog gives you a clear, end-to-end explanation of AWS VPC, Azure VNet, their components, and how both clouds connect securely in a hybrid or multi-cloud environment. Whether you’re a beginner or preparing for cloud interviews, this guide simplifies everything you need to know.
1. What Is AWS VPC?
AWS VPC (Virtual Private Cloud) is your private network inside AWS. Think of it as your isolated space where you deploy EC2, RDS, Lambda (in VPC mode), and other services.
A typical VPC includes:
CIDR block (e.g., 10.0.0.0/16)
Public and private subnets
Route tables
Internet Gateway (IGW)
NAT Gateway
Security Groups
Endpoints for S3/DynamoDB
The VPC provides complete control over network configuration, traffic routing, and resource isolation.
2. What Is Azure VNet?
Azure VNet (Virtual Network) is the Azure equivalent of AWS VPC. It serves as your private network where you deploy Azure VMs, Azure SQL, App Services (via integration), AKS clusters, and more.
A VNet includes:
CIDR block (e.g., 10.1.0.0/16)
Subnets (Web/App/DB tiers)
NSGs (Network Security Groups)
Azure NAT Gateway
Public IP + Load Balancer/Application Gateway
Just like AWS VPC, Azure VNet enables segmentation, security, routing control, and hybrid connectivity.
3. Public Subnet vs Private Subnet
Public Subnet (AWS & Azure)
Public subnets host resources that require direct access from the internet.
In AWS, public subnets use Internet Gateway (IGW).
In Azure, public access depends on Public IP + route to Internet.
Example resources:
Web servers
Bastion hosts
Load balancers
Private Subnet (AWS & Azure)
Private subnets host backend resources that should not be accessible from the internet.
Examples:
Application servers
Databases
Internal microservices
Outbound internet access is typically routed through:
AWS NAT Gateway
Azure NAT Gateway
Private subnets improve security, reduce attack surface, and enforce better architectural designs.
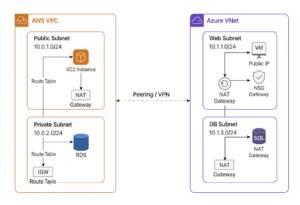
4. IGW, NAT, and Routing Explained
Internet Gateway (AWS)
Provides inbound/outbound access for public subnets.
Azure Public IP + Routing
Azure does not have an IGW object. Public internet access is enabled through:
Public IP
User-defined or system routes
NSG rules allowing traffic
NAT Gateway (AWS & Azure)
Both clouds use NAT Gateway for outbound-only access from private subnets.
This ensures:
✔ Servers can reach the internet for updates
✔ Internet cannot initiate traffic to them
Route Tables
Every subnet has a route table that governs traffic flow.
For example:
AWS Public Subnet Route:
0.0.0.0/0 → IGW
AWS Private Subnet Route:
0.0.0.0/0 → NAT Gateway
Azure Subnet Route:
0.0.0.0/0 → Internet (if public)
0.0.0.0/0 → NAT Gateway (if private)
5. Security: SG vs NSG
AWS Security Groups (SG)
Instance-level firewall
Stateful rules
Both inbound and outbound rules
Common for EC2, RDS, EKS
Azure Network Security Groups (NSG)
Applied at subnet or NIC level
Same stateful behavior
Control inbound + outbound ports
Both act as the primary security layer for cloud workloads.
6. Multi-Cloud Networking (AWS + Azure)
In modern architectures, businesses increasingly combine AWS and Azure to build resilient and scalable applications. To connect the two clouds, you have several options:
Option 1: Site-to-Site VPN (Most Common)
AWS VPN Gateway ↔ Azure VPN Gateway
Encrypted traffic through IPSec
Fast, cost-effective, easy to deploy
Option 2: ExpressRoute + Direct Connect
High-speed, dedicated private links
Enterprise-grade latency and reliability
Option 3: Third-Party Cloud Routers
Tools like:
Megaport
Aviatrix
Alkira
These offer advanced routing, segmentation, and multi-cloud operations.
After connecting AWS and Azure:
✔ Private subnets communicate directly
✔ No need for internet routing
✔ End-to-end secure-by-design architecture
✔ Ideal for hybrid workloads, DR, and migrations
7. Secure-By-Design Architecture Model
A multi-cloud secure model includes:
IAM/Entra for identity
VPC/VNet segmentation
Public → Private subnet separation
IGW/NAT for controlled traffic
SG/NSG for firewall
VPN/ExpressRoute for secure connectivity
VPC & VNet endpoints for private service access
This results in a scalable, secure, enterprise-ready network foundation.
Conclusion
AWS VPC and Azure VNet may use different names for their components, but the architecture principles remain the same: segmentation, controlled ingress/egress, strong identity, and secure connectivity. When combined into a multi-cloud architecture, these networks create a robust environment suitable for modern enterprise applications, hybrid workloads, and large-scale distributed systems.
💻 Project Files
💬 Join the Community
For more information about interview questions and answers Open-source Projects, DevOps and Cloud project, please stay tuned TechCareerHubs official website.